After the first run, security is maintained at all times even if nothing is done thereafter.
Leave 100 percents of the screen security to the MonitorDog
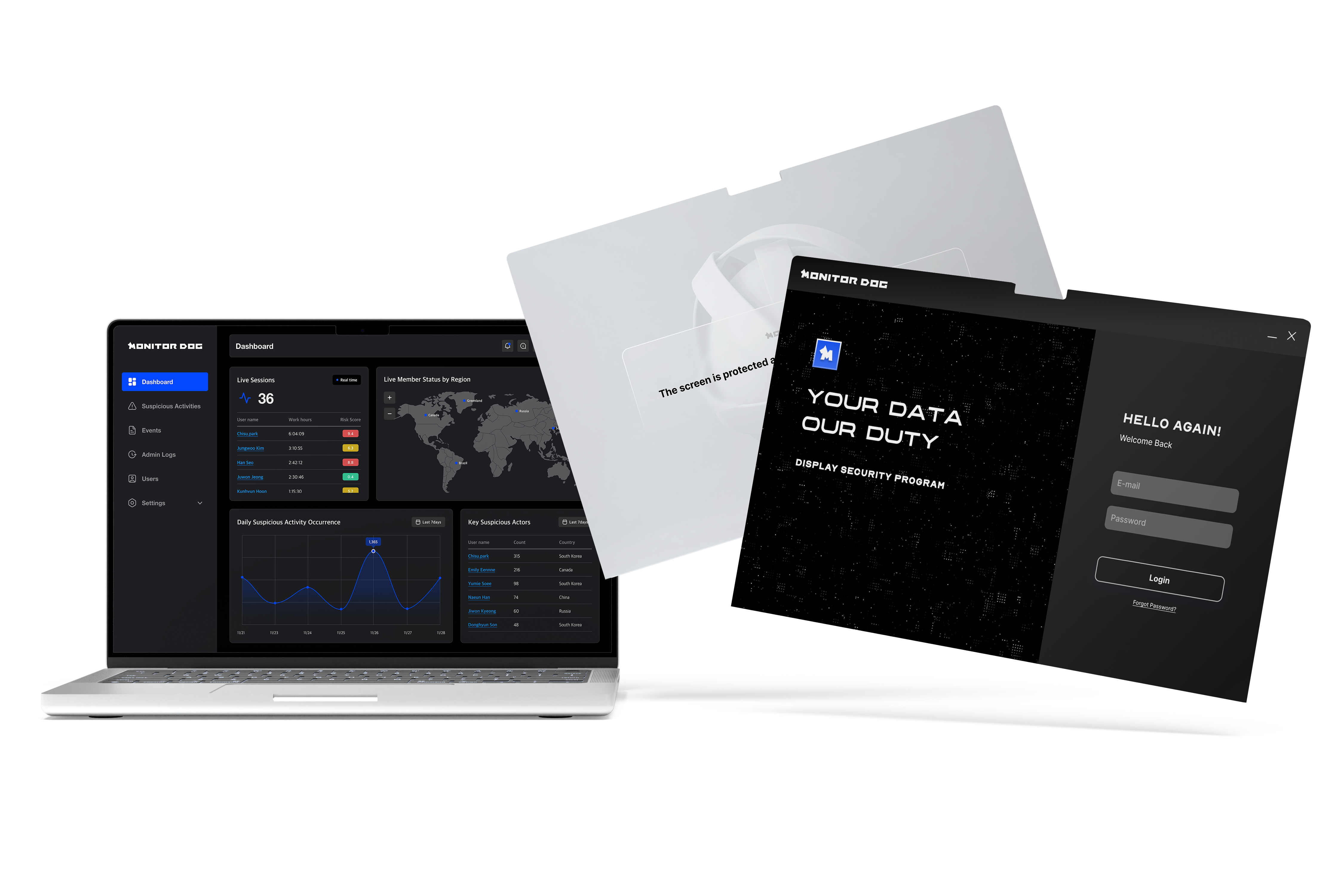
incomparable, High detection rate and fast speed

00ms
00%
00ms
Regardless of the data type,
Enhance the security
of all confidential data
with just one MonitorDog

Field of Introduction
What Data can we protect?













System requirements Specs





