
MONITORDOG
demo video
Necessity
Why MonitorDog?
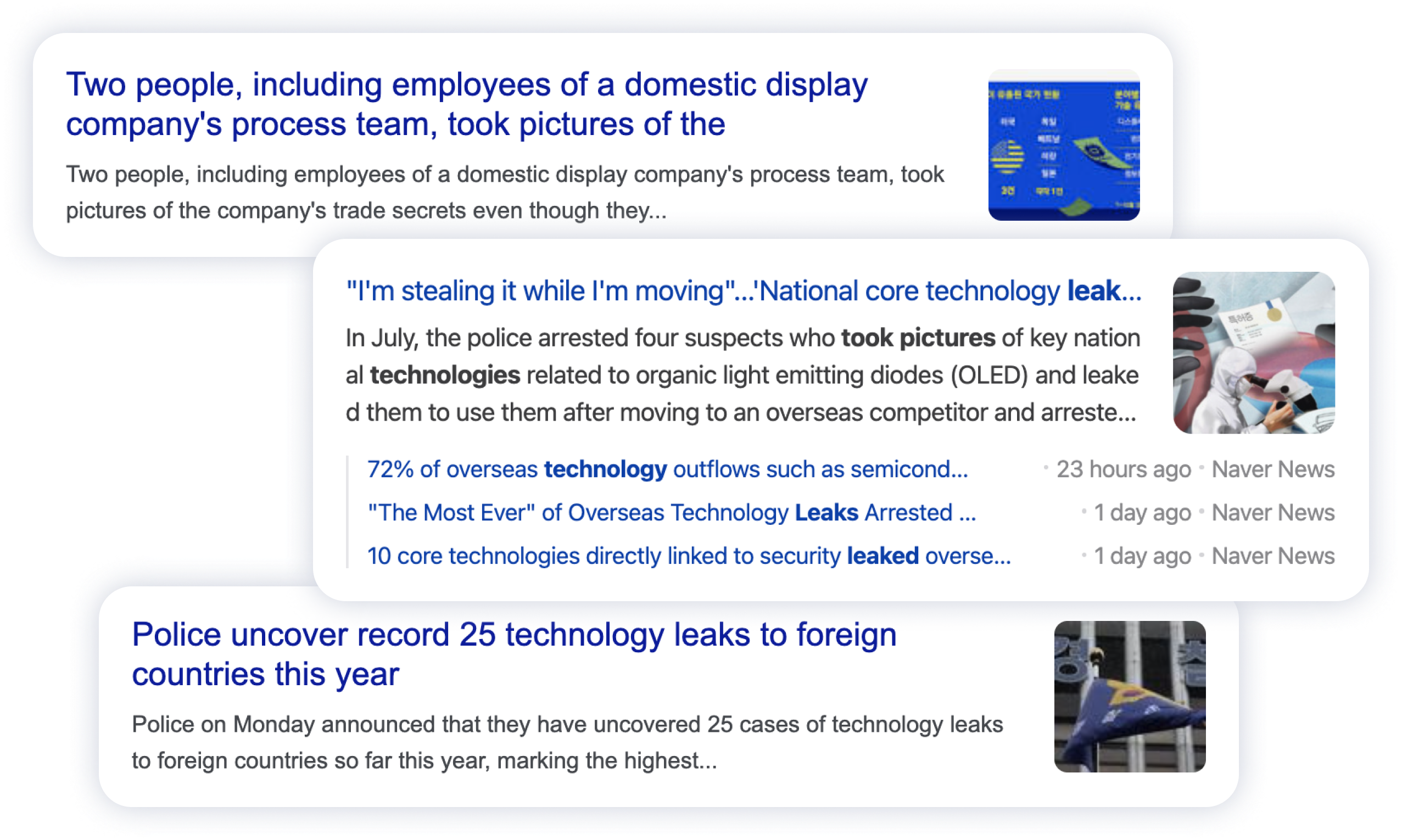
With telecommuting becoming widespread,
cases of confidential information leakage
through smartphone filming continue to grow.
Conventional screen security solutions
such as capture prevention are no longer effective
against unauthorized smartphone photography.
Data leakage attempts are evolving.
New security solutions are essential.
The answer is 
Maintain screen security even when working from home or on a business trip.
Work freely and securely anywhere
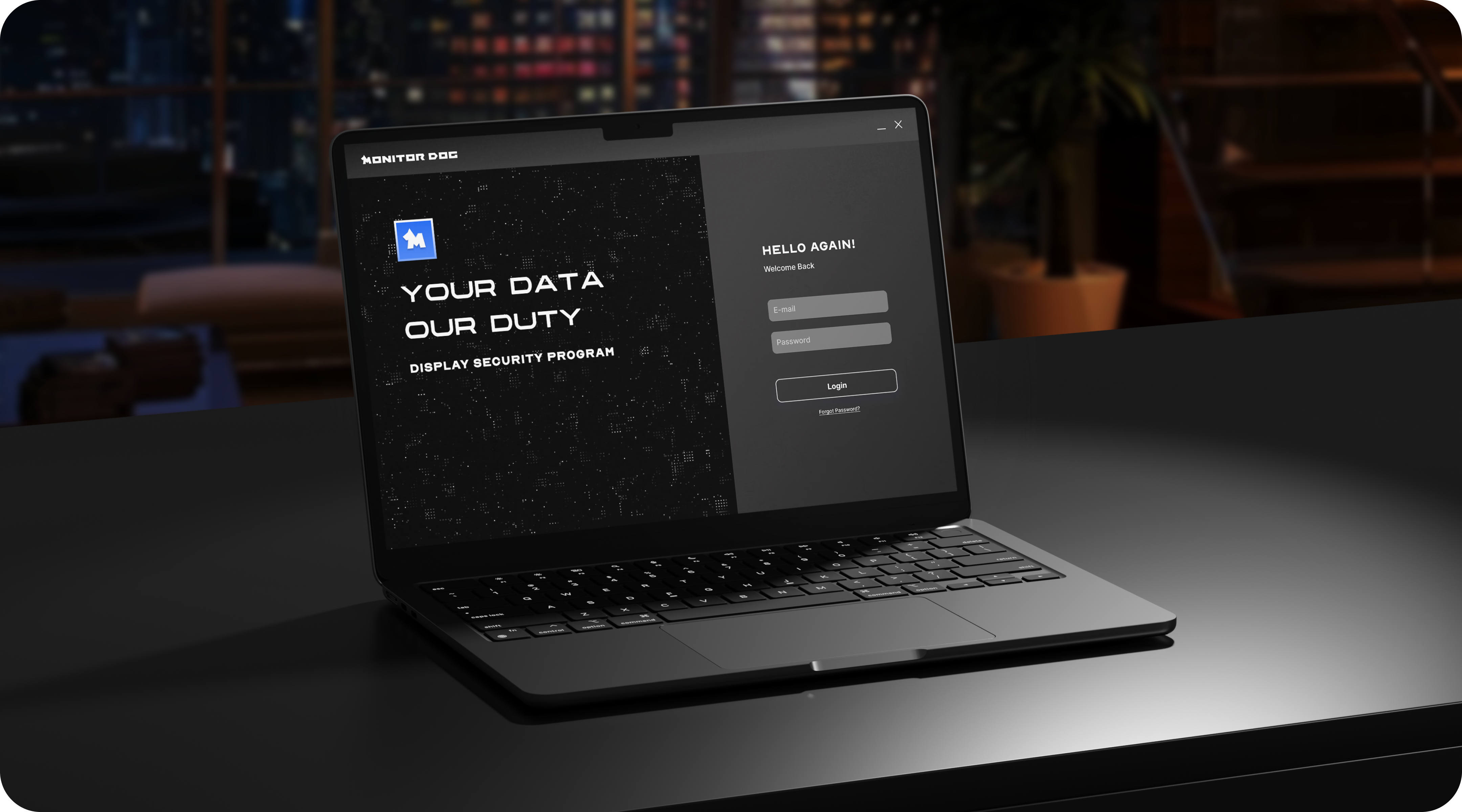

If I use a MONITORDOG
How will my company's security change?
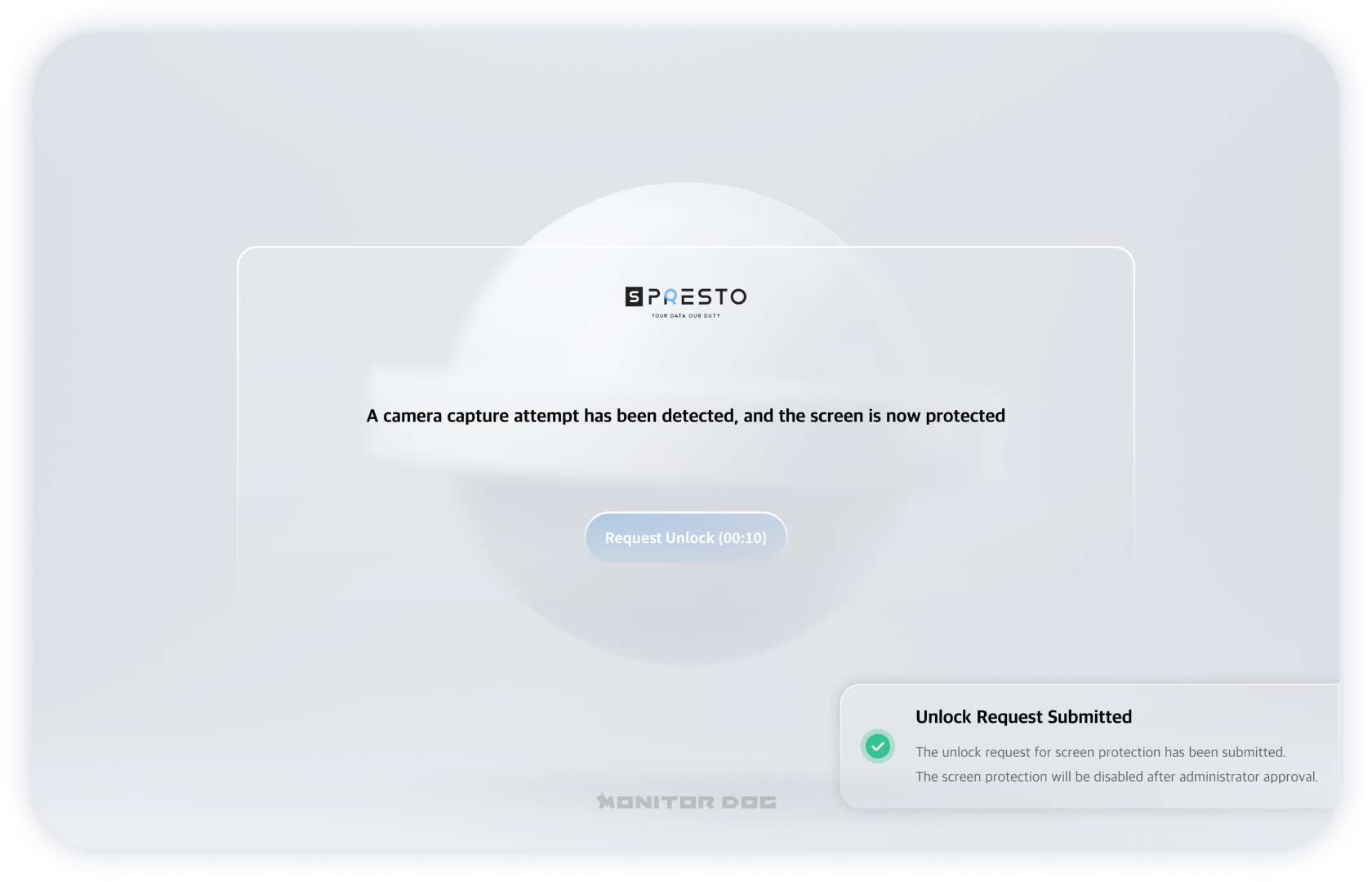
Blocking the source of
the screen shot
It provides real-time detection and alerts for monitor screen photography using smartphones or similar devices, which was an area overlooked by conventional security systems.
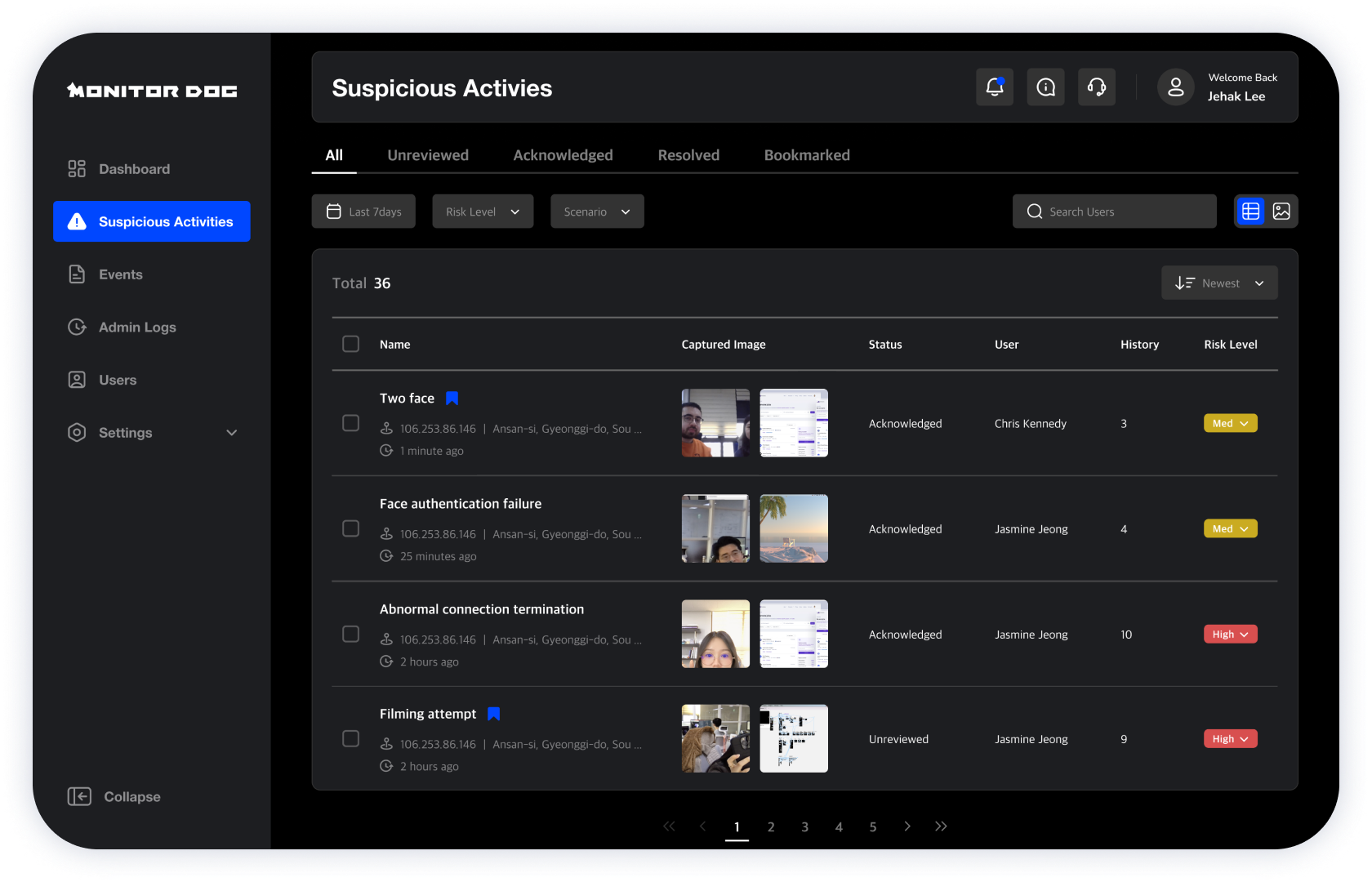
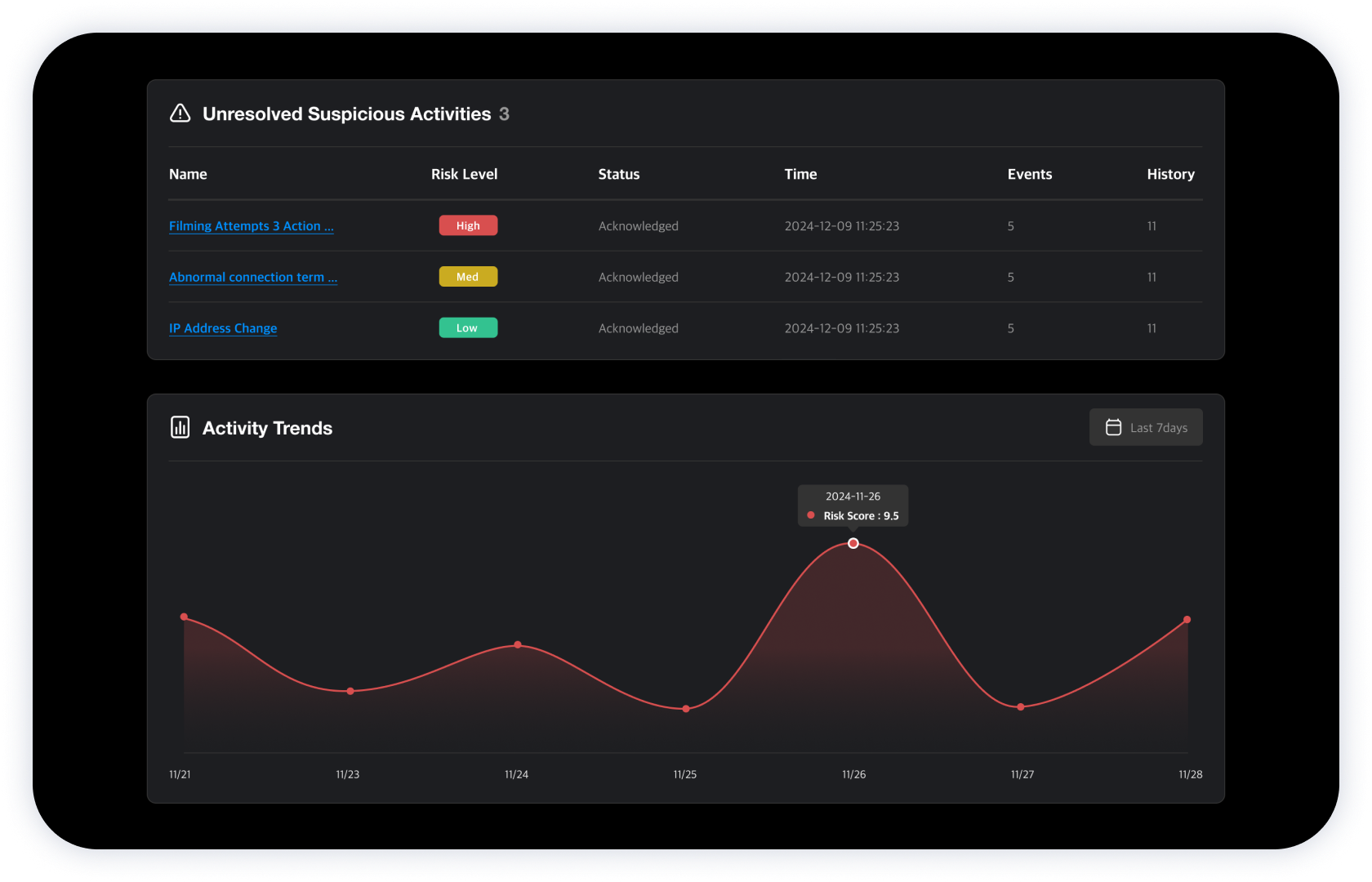
Abnormal behavior
report
It detects any attempt to bypass the security system—such as logout, network disconnection, or forced program termination—as well as security breaches like smartphone photography attempts or screen emptying.
Security Insights
You can identify users with frequent suspected behavior, along with webcam images captured at the time of each event.